2025 DownUnder CTF - Writeup
Author: 堇姬 Naup
CTFteam: Squid Proxy Lovers
Rank: 8th
前言
I was quite busy during this competition, so I only solved two challenges (I’ll just write more interesting one challenge — It is kernel pwn). This was also my first time playing a CTF together with SPL.
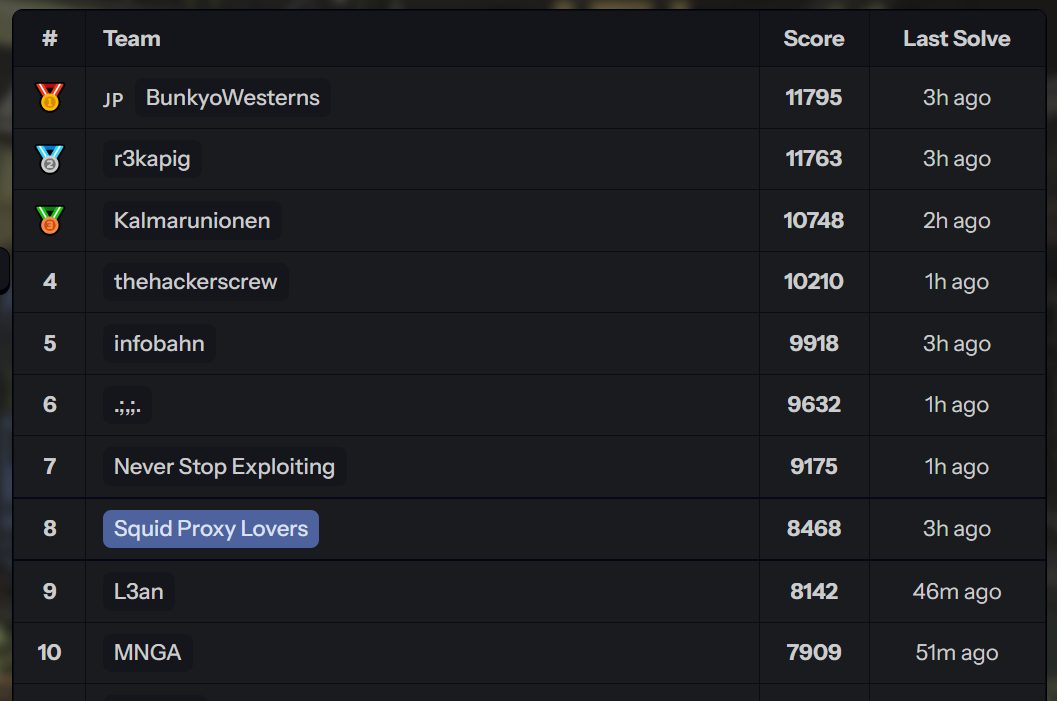
It looks so cool, lol.
backdoor
analyze
1 |
|
It add a new syscall on syscall table.
Its syscall number is 1337
1 | +++ b/arch/x86/kernel/backdoor.c |
This section is the implementation of the syscall.
It need to provide two arguments. (shellcode and size)
We can get one rwx page and jump to execute your shellcode.
When it execute your shellcode, it will clear all registers and xmm value.
1 | qemu-system-x86_64 \ |
You can check qemu startup script.
It open KASLR、SMAP、SMEP and KPTI
How to EoP
We can run arbitary shellcode in kernel, so many way can EoP.
But, we don’t have kernel base.
So the first goal is to try to leak it. (I suspect that the key point of this challenge is to leak the kernel base, since the registers were deliberately cleared.)
My sulution is use MSR(IA32_LSTAR = 0xC0000082)
It will return entry_SYSCALL_64 address.
This address is kernel text base (rax).
Put kernel base on r8 and overwrite modprobe_path, and then return to userspace.
1 | mov ecx, 0xC0000082 |
Use socket trigger modprobe_path, you can get flag.
exploit
upload script
1 | from pwn import * |
exploit
1 |
|
DUCTF{n0_r3g1st3rs_n0_pr0bl3m!}
